Android Jailbreak - fl3xbl0w
Reverse engineering project. It started with the Bowflex Treadmill 22 but ended up being generalized for any Android machine sold by Nautilus Inc. (Nautilus, Bowflex, Schwinn).
This method relies on the Bowflex Console’s specs being too slow for today’s software (it only has 2Gb of RAM on the Android board). Because of that, and if we are faster than the tablet, we can jailbreak from Nautilus’s AppMonitorService.
Could it be called a brute force attack?
You can restart the machine at any point in the process, and everything will be as it should. There is no risk on the software side for doing so. Give it a try!
Requirements
- A USB keyboard (wired or wireless via a USB dongle) with media buttons for Home, Back.
- Quick fingers! (the “intense part” must happen in about a second)
- A computer with adb (download link)
I used a Logitech K600, but any keyboard with those keys should work:

Bluetooth keyboards seem unable to pair through JRNY.
Tips
- Don’t try to “get it right” from the start. It takes a few attempts to figure out “where the buttons appear on the screen” so you can build some muscle memory for the tapping actions.
- DO NOT HIT THE SCREEN HARD! Being quick doesn’t mean breaking it. I am not responsible for people hitting their screens too hard.
Instructions
First, let’s turn on the machine and connect the USB keyboard to the Bowflex Console. You can find it on the right side:

Let’s make sure the keyboard works by pressing the “Home” button on the keyboard. It should cause the JRNY app to restart.
Android has a shortcut to close the current app through the “Back” button if you hold it down for a second or so. Let’s play a bit with the “Back” button - we’re going to continuously close the JRNY app as soon as it reopens until a new dialog starts to appear:
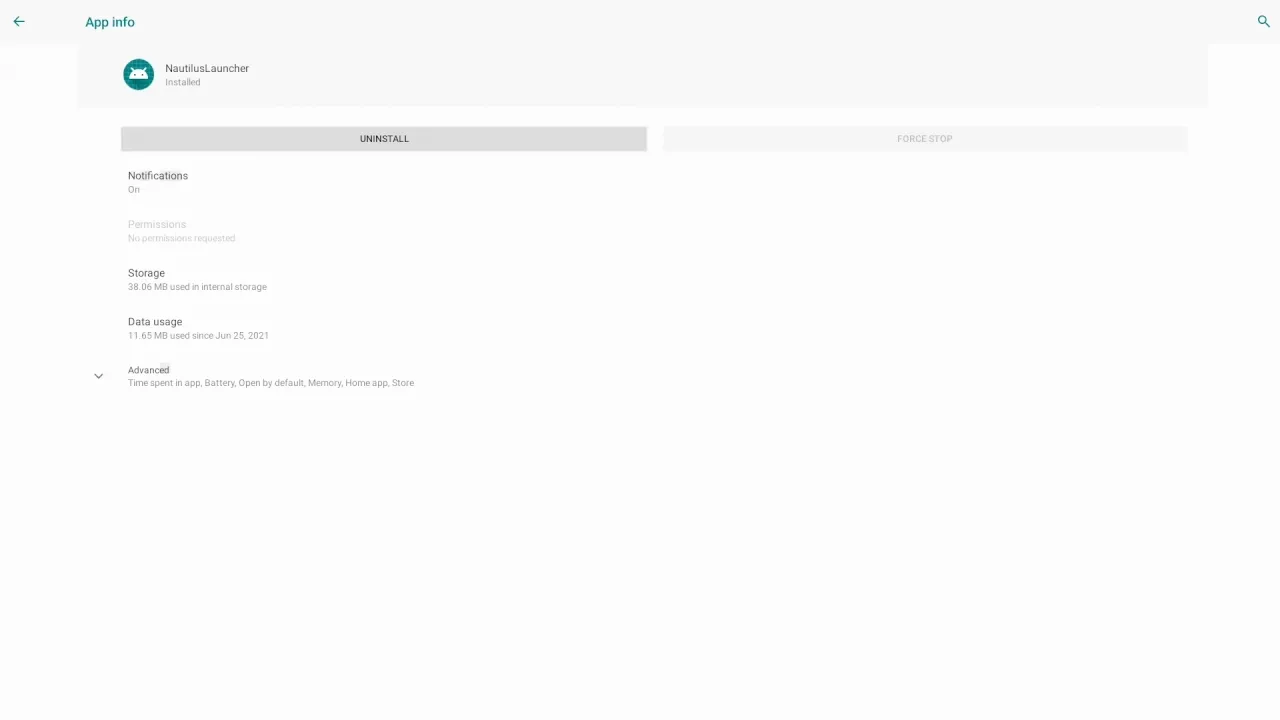
Ok, now the fun part: That dialog belongs to Android’s stock “fault verification system”. We just “forced Android to think” that NautilusLauncher is bad (good!). Let’s exploit through that dialog.
As soon as it appears, tap on “App info”. By clicking on “App info” we’re going to open the Settings app (which is on the AppMonitorService denied list). It will close in about a second, so we have to be quick! Tap on the “FORCE STOP” button, and then tap on “OK”.

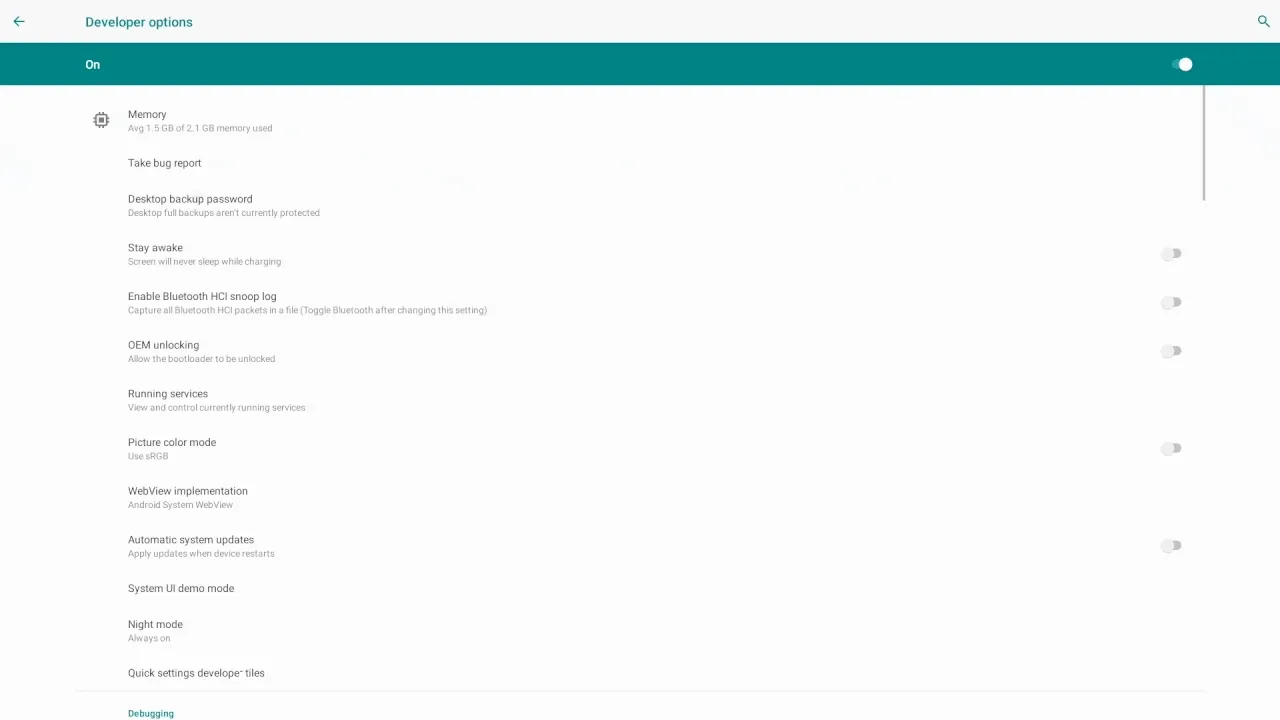
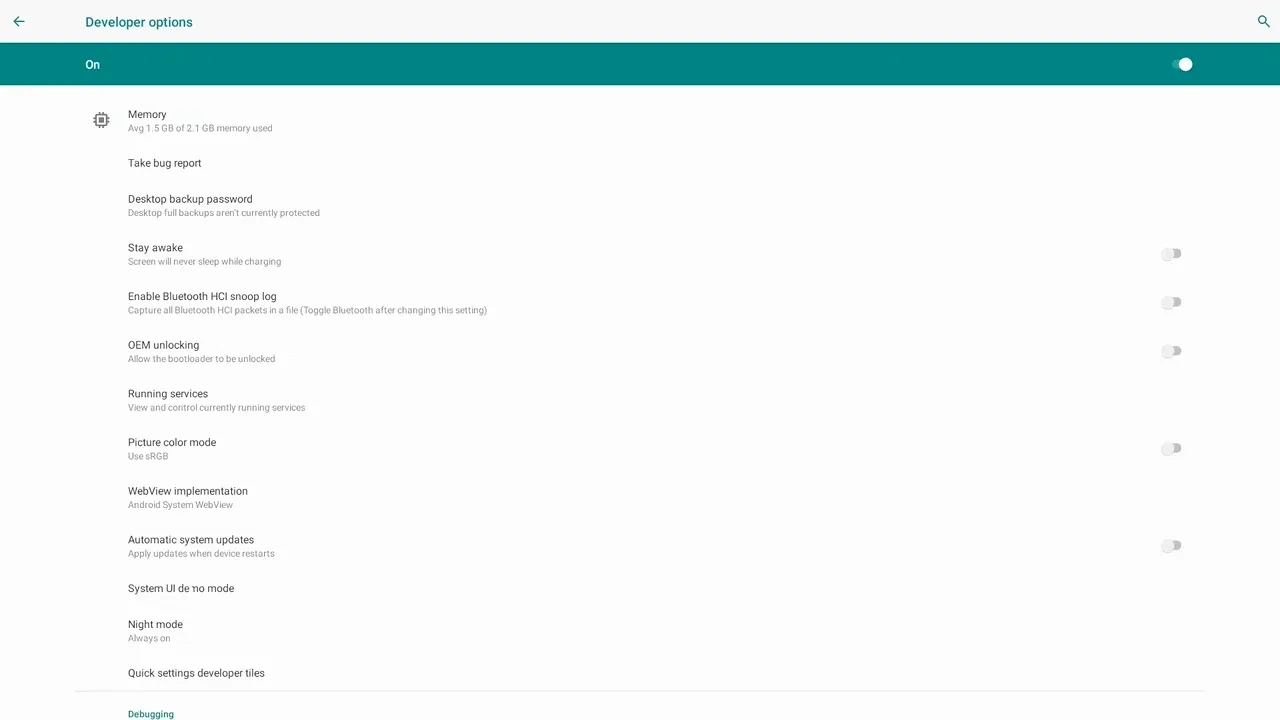
As soon as you can click “OK”, you can rest (good exercise, huh?). Now let’s proceed with the findings on Reddit. We’re going to enable adb by clicking on the “magnifying glass” icon in the top right corner and searching for “Developer options”:
Find the Console’s IP address. The easiest way is through the Wi-Fi Settings:
Now that adb is enabled and we have the IP address, let’s jump to a computer and connect with adb. Open a terminal and run adb connect <IP Address> (in my case 10.0.0.205):
> adb connect 10.0.0.205
connected to 10.0.0.205:5555It will ask for a confirmation on screen the first time you connect remotely through adb.
Let’s create an empty file inside /sdcard/Pictures/ called nautilus. You can read more about the “why” in Bowflex Quirks.
> adb shell touch /sdcard/Pictures/nautilusNow let’s restore some functionalities. Send the following commands through your terminal:
> adb shell settings put secure ntls_launcher_preference 0
> adb shell settings put secure navigationbar_switch 1
> adb shell settings put secure notification_switch 1
> adb shell settings put secure statusbar_switch 1You’ll see the UI appear:
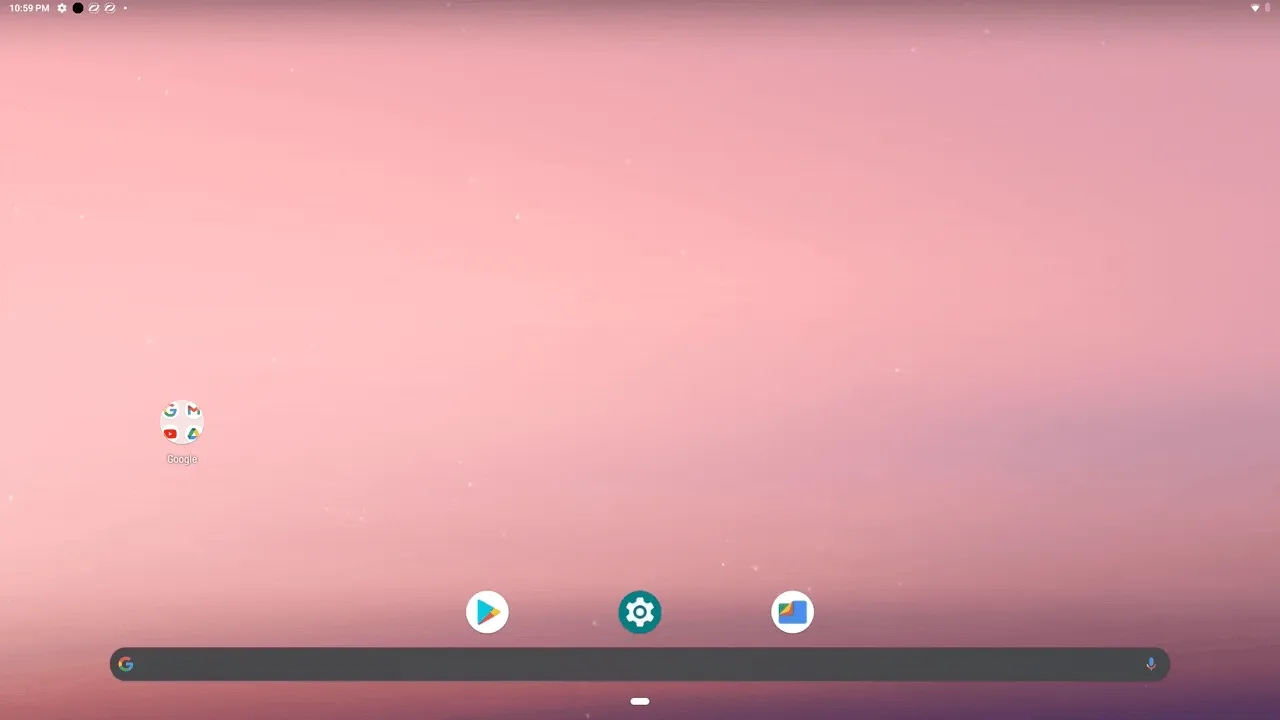
There’s one final step - changing the default launcher. Search for “Default apps” and set Quickstep as the home app:

You are now free!
This state will remain as long as NautilusLauncher is forced to stop. It persists through reboots.
If you want to go back to “stock” just open the NautilusLauncher app (I strongly suggest you created the /sdcard/Pictures/nautilus file beforehand):
Notes on the “Lockdown System”
NautilusLauncher is the default “Android launcher”, which means that if the JRNY app closes, it will immediately “reopen”.
There’s also another “security lock”, a foreground service in the NautilusLauncher apk, called AppMonitorService. By decompiling the apk, you can see three interesting variables:
public static final int MonitorIntervalSeconds = 1;
// Some more variables
private static String[] TargtedAppsToKill = {"com.android.vending", "com.android.settings", "com.android.chrome", "com.google.android.gm", "com.google.android.youtube"};
private static String[] TargtedAppsToBackground = {"com.google.android.googlequicksearchbox:interactor", "com.google.android.googlequicksearchbox:search", "com.google.android.googlequicksearchbox", "com.android.launcher3", "com.google.android.inputmethod.latin"};And so that service is “actively protecting” the lockdown. With each app closure (through holding the “Back” button), there will be an attempt to reopen JRNY. By forcing its closure, we also deactivate all foreground services.
(any typos you may see in the code backups come from Nautilus’s own developers, not mine)